Getting Started
This page describes how to get started with the Knowledge Model API in a simple way using Postman.
Prerequisites
- You need to have a Knowledge Model available in your team.
- You must request the activation of the API in your Celonis Platform Team to your Celonis account team.
Authentication
The authentication options applicable to all Celonis APIs are described here.
Authorization
OAuth Scopes for the Knowledge Model API
OAuth clients for Knowledge Model API should be configured with the scope:
-
intelligence.knowledge-models:read
Client Permissions for the Knowledge Model API
You must set the right permissions and ensure the User API Key or the Application API Key leveraged for authorization purposes has access to the Celonis Platform Studio package containing the Knowledge Model(s) you would like to access through the Knowledge Model API.
You can grant access permissions by following these steps:
- Go to the Studio package.
-
Click the three dots and select
Permissionsfrom the pop-up menu. -
Search for the User (if you are using a
Bearer token
) or AppKey (if you are using an
AppKey
) and grant at least
USE PACKAGErights.
Consuming the Knowledge Model API
Once you have completed the previous steps, you can start making requests to the API. For that you will use Postman (or any other REST client), which you should already have installed in our system.
- Go to File > New... and select "HTTP Request". Once you do this, you should see something like this:
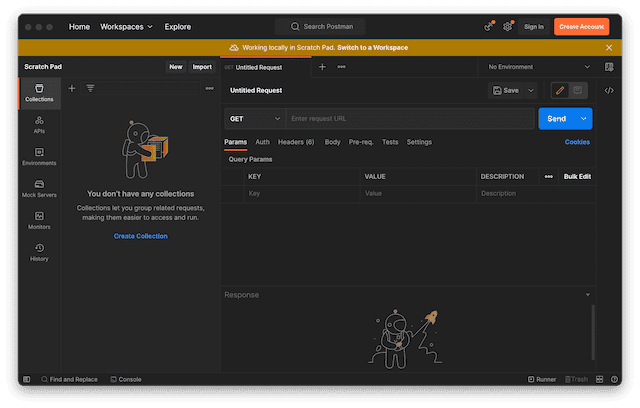
- Enter the request URL next to the Send button. For this URL you will use the one from the "Determine the URL for your team" section: https://dev.us-2.celonis.cloud/intelligence/api .
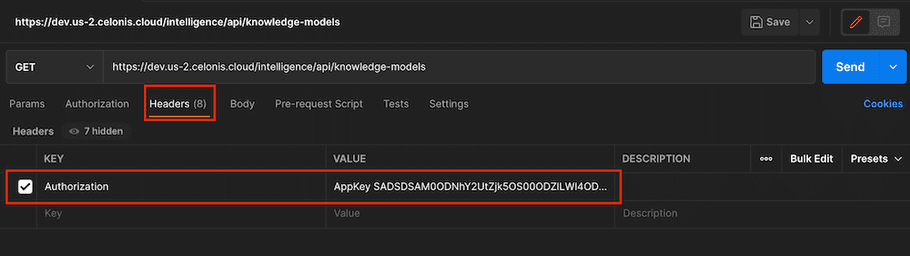
- Now you need to set your API or Application Key in order to authenticate our requests. To do this, click on the Headers tab beneath the URL you just entered. Enter "Authorization" as the Key and for Value, enter:
-
Bearer <YOUR_KEY>if you have a User API Key -
AppKey <YOUR_KEY>if you have a AppKey
In the following example, you have an AppKey:
Getting the list of Knowledge Models
Once you have completed the steps above, you should now be able to start getting some data. You will start getting the full list of Knowledge Models that your API token has access to.
First, append "/knowledge-models" to the URL you used in the previous steps: https://dev.us-2.celonis.cloud/intelligence/api/knowledge-models.
After that, click the Send button next to the URL and you should see something like:
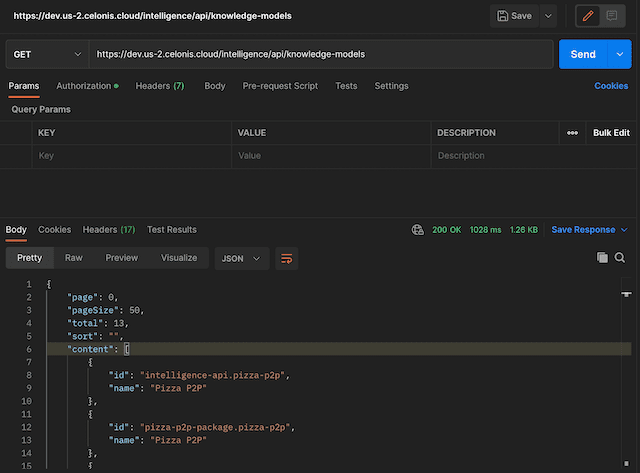
In the Content section, you will see a list of all your Knowledge Models. The Knowledge Models will be divided into pages. By default, the page size will be 50. If you have more than 50 Knowledge Models, you can navigate to the following page, adding a "page" query parameter. The pages start at 0, so you can display the second page by setting a page value of 1.
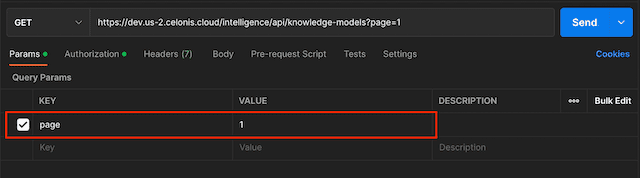
In this example, this is not needed as there are only 13 Knowledge Models. However, you might want to specify other query parameters such as:
- pageSize: Sets the size of each page.
- sort: Sort the results by id or name.
You can check the full list of parameters and possible responses from this page.
You can also check the full list of possible errors that you can receive in the API, in case you need to troubleshoot any issue.
In this quick guide, YOU managed to create your first request to the Knowledge Model API. If you would like to do more advanced requests, we recommend that you check the full list of capabilities of this API or review this guide that walks you through the rest of schema endpoints.